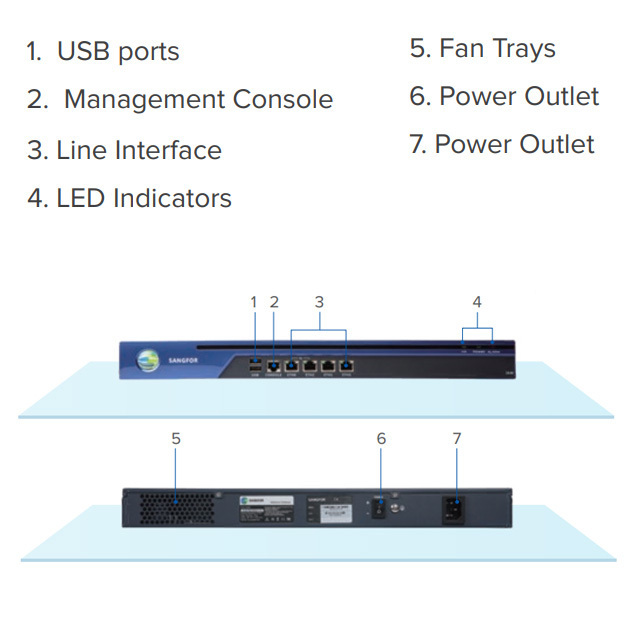
- Product Details
- {{item.text}}
Quick Details
-
Throughput:
-
400Mbps
-
Brand Name:
-
SANGFOR
-
Model Number:
-
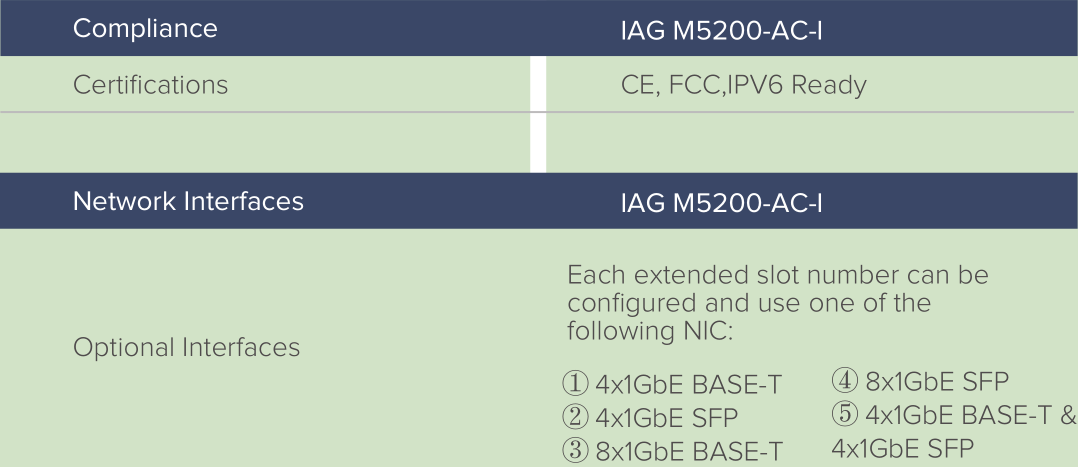
SANGFOR IAG M5200-AC-I
-
Place of Origin:
-
Guangdong, China
Quick Details
-
Type:
-
Wired & Wireless
-
VPN Support:
-
Yes
-
Simultaneous Sessions:
-
180,000
-
Throughput:
-
400Mbps
-
Brand Name:
-
SANGFOR
-
Model Number:
-
SANGFOR IAG M5200-AC-I
-
Place of Origin:
-
Guangdong, China
Recommend Products
Product Description

|
Performance & Capacity
|
IAG M5200-AC-I
|
|
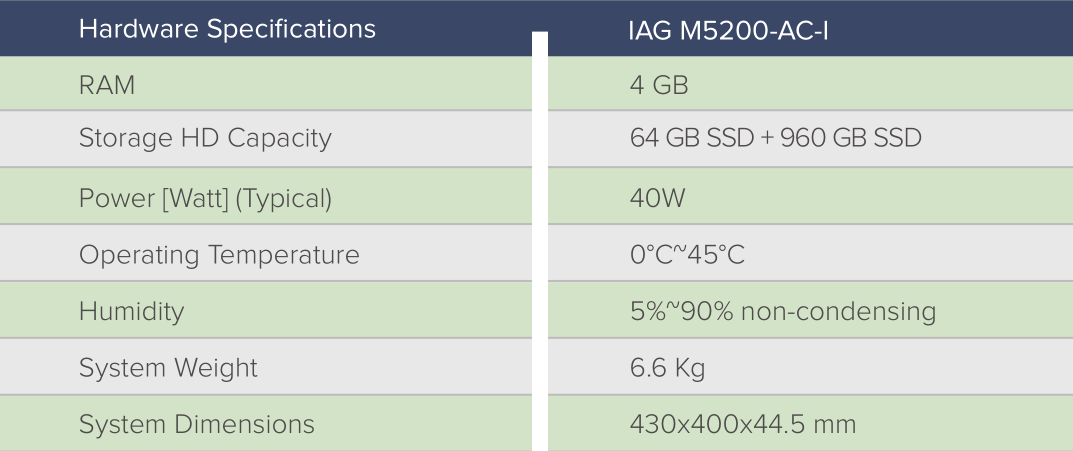
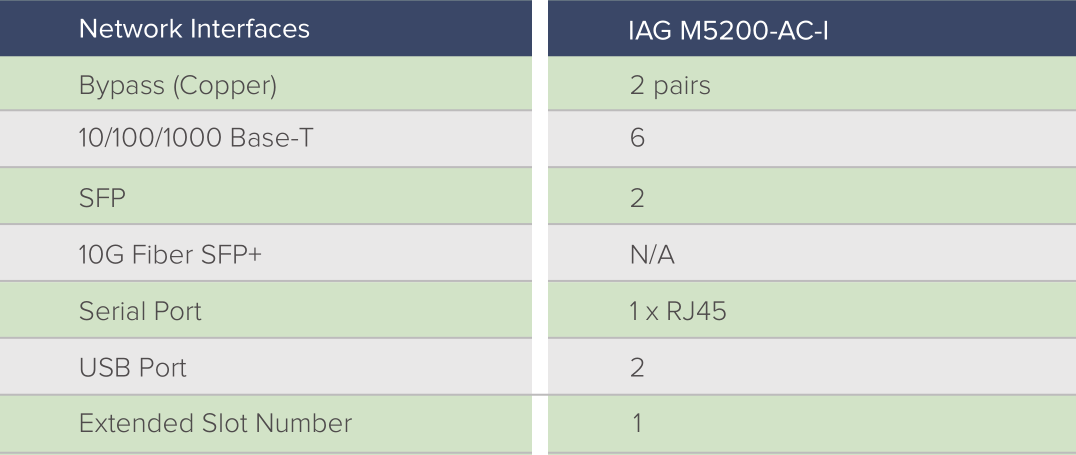
Dimension
|
1U
|
|
Application Layer Throughput
|
400Mbps
|
|
Recommended Concurrent Users
|
2,000
|
|
Concurrent Connections(TCP)
|
180,000
|
|
New Connections(TCP)
|
4,000
|
|
Redundancy Power Supply
|
N/A
|
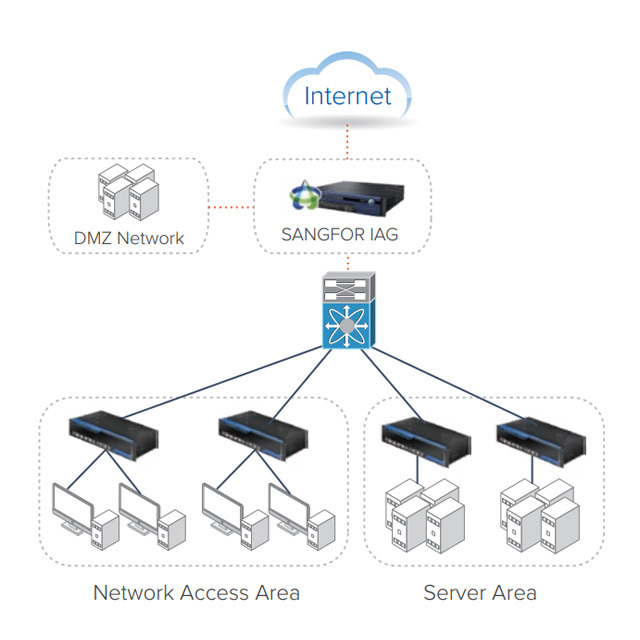
Deployment Modes
Key Features
1、Unified Management of all Clients in the Entire Network
Sangfor IAG can efectively control both Wired and Wireless networks,
achieving Unified Management of all clients in the entire network. Rich
and flexible authentication methods, such as username/password,
IP/MAC binding, etc., as well as value-added marketing authentication
methods (QR code, SMS, WeChat, Facebook, Alipay, etc.) are available
in Sangfor IAG. It can also control permissions based on user,
application, location and client types.
2、Intelligent Control with Visibility of User Behavior & Trafc
Sangfor IAG is able to manage and control network applications & web
browsing more conveniently and accurately. It has one of the largest
application signature database and URL database, which are updated
every 2 weeks. Its bulk management mode for large enterprises greatly
improves the productivity and efciency
Thanks to three unique major trafc management technologies (Dynamic
Trafc Control, Intelligent Flow Control, Quota Control) of Sangfor IAG,
the bandwidth utilization can be improved by more than 30%
3、Simple & Intuitive Reporting for Simpler Network Management
SANGFOR IAG is built-in with an Advanced Report Center, which supports
various customized reports based on trafc statistics, queries, ranking,
times and behavior of user & user groups, helping enterprises analyze
the root causes of all network issues. IT managers are provided with all
the detailed information they need to know about their network, including
Internet access activities, bandwidth consumption and viewed contents.
Reports are self-generated and automatically & regularly sent to an
appointed e-mail address to efectively assist in the network design,
secure it and optimize the usage of the bandwidth.
4、Business Intelligence
The Sangfor Business Intelligence platform is based on Hadoop and
adapted to Mapreduce data process technology & NoSQL database to
perform TB data query’ s in seconds and makes data processing more
efcient and intelligent. Trafc identification distinguishes between
user and machine trafc while the Graph Computing and Machine
Learning performs modeling analysis of all trafc. Scenario based
applications brings you the best ever operation experience.
1、Unified Management of all Clients in the Entire Network
Sangfor IAG can efectively control both Wired and Wireless networks,
achieving Unified Management of all clients in the entire network. Rich
and flexible authentication methods, such as username/password,
IP/MAC binding, etc., as well as value-added marketing authentication
methods (QR code, SMS, WeChat, Facebook, Alipay, etc.) are available
in Sangfor IAG. It can also control permissions based on user,
application, location and client types.
2、Intelligent Control with Visibility of User Behavior & Trafc
Sangfor IAG is able to manage and control network applications & web
browsing more conveniently and accurately. It has one of the largest
application signature database and URL database, which are updated
every 2 weeks. Its bulk management mode for large enterprises greatly
improves the productivity and efciency
Thanks to three unique major trafc management technologies (Dynamic
Trafc Control, Intelligent Flow Control, Quota Control) of Sangfor IAG,
the bandwidth utilization can be improved by more than 30%
3、Simple & Intuitive Reporting for Simpler Network Management
SANGFOR IAG is built-in with an Advanced Report Center, which supports
various customized reports based on trafc statistics, queries, ranking,
times and behavior of user & user groups, helping enterprises analyze
the root causes of all network issues. IT managers are provided with all
the detailed information they need to know about their network, including
Internet access activities, bandwidth consumption and viewed contents.
Reports are self-generated and automatically & regularly sent to an
appointed e-mail address to efectively assist in the network design,
secure it and optimize the usage of the bandwidth.
4、Business Intelligence
The Sangfor Business Intelligence platform is based on Hadoop and
adapted to Mapreduce data process technology & NoSQL database to
perform TB data query’ s in seconds and makes data processing more
efcient and intelligent. Trafc identification distinguishes between
user and machine trafc while the Graph Computing and Machine
Learning performs modeling analysis of all trafc. Scenario based
applications brings you the best ever operation experience.
Software Features
1、User Authentication and Management
Mapping and identifying users | IP/MAC binding, hostname, USB
Key, SMS, QR-Code, Portal, WeChat, Facebook, etc. | User
accounts importing and synchronizing from LDAP, CAM3, etc. |
SSO integration: AD/POP3/Proxy/Radius, 3rd party authentication
device and DB Serve
2、Access Control | SSL Decryption
Application control | URL filtering | Search Engine Control,
Enhanced Email/IM control | File filtering | SSL traffic control |
Illegal Wi-Fi.
3、Proxy Avoidance Protection
Anti-Proxy with Endpoint Secure Integration | Anti-proxy with IAG
application signature database.
4、Bandwidth Management
BM according to specific object/policy | International & Domestic
BM | Bandwidth Guarantee & Limitation | Multi-level SON Channel
| Dynamic BM | Virtual line | Multiplexing and intelligent routing.
5、Report Center
Report based on application traffic, user behavior, etc. | Graphical
reports by counts, ranking, comparison, trends analysis with
statistics, pie, bar, line chart, etc. | Real time report | Content log
for IM chat records, emails, forum posts, etc. | Customized CIO
report | Built-in internal and optional external report center |
Export to CSV or PDF format.
6、Management & Deployment
Centralized management support | Proxy functions: HTTP/HTTPS
Sockets 4/5, ICAP | HA support (A/A,A/P), Hardware bypass |
Deployment mode: Route, Bridge, Double Bridge, Bypass,
Single-arm | Built-in Firewall | IPsec VPN.
7、Endpoint Security Posture
Ingress Client Based (Agent) | Ingress Client rule based on Login
domain, operating system, process, file, registry, task, patch,
access check, access control, external device control, windows
account, software check, anti-defacement and anti-virus software
related to update and database version | Traffic Based
(Agentless) | Traffic Based rule based on Check personal
software and enterprise software for anti-virus destination server
IP heartbeat.
8、Asset Management
Asset Discovery: Identify and list of IOT devices, advanced search
and filter, export to csv | Asset Classification: Categorize endpoint
type based on host, mobile endpoint, network device, dumb
endpoint, medical equipment, network endpoint sharing and
custom.
1、User Authentication and Management
Mapping and identifying users | IP/MAC binding, hostname, USB
Key, SMS, QR-Code, Portal, WeChat, Facebook, etc. | User
accounts importing and synchronizing from LDAP, CAM3, etc. |
SSO integration: AD/POP3/Proxy/Radius, 3rd party authentication
device and DB Serve
2、Access Control | SSL Decryption
Application control | URL filtering | Search Engine Control,
Enhanced Email/IM control | File filtering | SSL traffic control |
Illegal Wi-Fi.
3、Proxy Avoidance Protection
Anti-Proxy with Endpoint Secure Integration | Anti-proxy with IAG
application signature database.
4、Bandwidth Management
BM according to specific object/policy | International & Domestic
BM | Bandwidth Guarantee & Limitation | Multi-level SON Channel
| Dynamic BM | Virtual line | Multiplexing and intelligent routing.
5、Report Center
Report based on application traffic, user behavior, etc. | Graphical
reports by counts, ranking, comparison, trends analysis with
statistics, pie, bar, line chart, etc. | Real time report | Content log
for IM chat records, emails, forum posts, etc. | Customized CIO
report | Built-in internal and optional external report center |
Export to CSV or PDF format.
6、Management & Deployment
Centralized management support | Proxy functions: HTTP/HTTPS
Sockets 4/5, ICAP | HA support (A/A,A/P), Hardware bypass |
Deployment mode: Route, Bridge, Double Bridge, Bypass,
Single-arm | Built-in Firewall | IPsec VPN.
7、Endpoint Security Posture
Ingress Client Based (Agent) | Ingress Client rule based on Login
domain, operating system, process, file, registry, task, patch,
access check, access control, external device control, windows
account, software check, anti-defacement and anti-virus software
related to update and database version | Traffic Based
(Agentless) | Traffic Based rule based on Check personal
software and enterprise software for anti-virus destination server
IP heartbeat.
8、Asset Management
Asset Discovery: Identify and list of IOT devices, advanced search
and filter, export to csv | Asset Classification: Categorize endpoint
type based on host, mobile endpoint, network device, dumb
endpoint, medical equipment, network endpoint sharing and
custom.
Hot Searches